A firewall review assesses your company’s network security, aligning with business needs and risk tolerance to mitigate cyber threats.
Understanding the Importance of Regular Firewall Audits
Businesses today often work with multiple firewall vendors, complicating a unified cybersecurity stance. A regular firewall review helps maintain a strong security posture amid evolving data protection demands.
Define Audit Plan Goals and Scope
Every firewall audit begins by defining clear objectives, which may include:
- Compliance Documentation: Ensuring adherence to PCI DSS, HIPAA, NIST, GDPR, and other regulations.
- Reducing Attack Surface: Removing outdated or unused firewall rules.
- Performance Optimization: Simplifying rules to improve network speed and efficiency.
Analyze Network Topology and Security Zones
Building effective security zones (e.g., DMZs) helps isolate network segments, minimizing potential attack impacts. Reviewing firewall locations, roles, and connections is essential for mapping out the network topology.
Collect Essential Audit Documentation
For efficient firewall reviews, gather these documents for your security team:
- Security Policies: Detailing internal best practices and controls.
- Firewall Logs: Including protocols, IP addresses, and subnets for tracking activity.
- Risk Assessments: Documenting risk mitigation actions.
- Rulesets: Configurations that define firewall permissions.
- Previous Audit Reports: Summaries of past findings and actions taken.
Evaluate Firewall Rule Placement and Prioritization
Arrange firewall rules logically, with high-priority rules at the top. Best practices include:
- Allowing specific, defined traffic
- Blocking all other traffic by default
Specific rules should detail source IPs, destination IPs, ports, and protocols, like TCP, ICMP, or UDP.
Identify and Address Unused Objects
Unused objects, such as inactive IPs, services, or applications, can create vulnerabilities. Reviewing and removing these objects is vital for a secure network.
Review Access Control Lists (ACLs)
ACLs regulate network access from external sources. Avoid permissive rules that create risks. Effective practices include:
- Limiting source and destination traffic
- Specifying IPs rather than using “any”
Verify User Roles and Access Privileges
Access reviews ensure users have only necessary permissions. For a firewall audit, confirm:
- Consistency in roles across vendors
- Updated permissions following role or IP changes
Examine Change Management Procedures
Firewalls require a structured change management process. Track modifications, including risks, impacts, and mitigation strategies.
Secure Firewall Hardware and Software
Update firewall firmware and operating systems to prevent unauthorized access. Regular vulnerability scans help address potential issues promptly.
Audit Firewall Logs
Firewall logs monitor network activities and help identify security incidents. Key events to track include:
- Blocked and permitted connections
- User activity and protocol usage
Conduct Risk Assessments
Prioritize documenting risk assessments both before and after changes to ensure minimal impact on business continuity and security compliance.
Resolve Issues and Test New Firewall Rules
After identifying audit issues, address them and test the revised firewall configurations. Testing minimizes operational impact before full deployment.
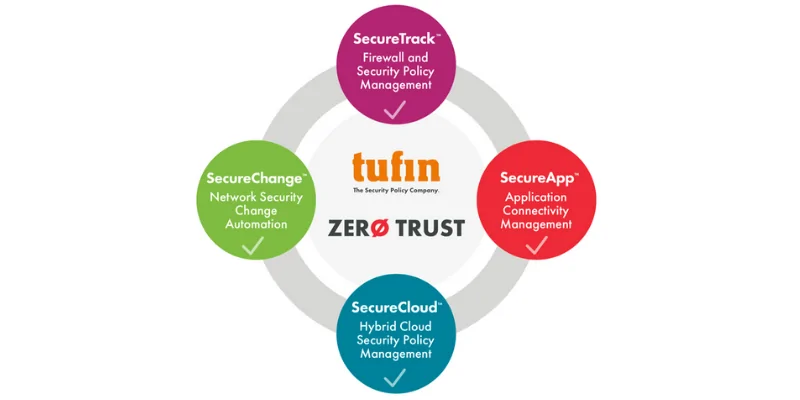
Streamline Documentation with Tufin
Tufin’s platform enables firewall management with Unified Security Policies, facilitating multi-cloud consistency and detailed compliance reports for faster audit readiness.
Tufin Orchestration Suite for Ukrainian IT Market
As a unique cybersecurity solution, Tufin Orchestration Suite is now accessible in Ukraine through NWU, supporting SOC teams in Ukrainian organizations.
Contact NWU for consultations on Tufin’s latest features and purchasing options.