The cybersecurity industry is facing a new challenge — AI-generated attacks. With the rapid development of generative AI, attackers have gained access to powerful tools that allow them to create highly targeted attacks without deep technical knowledge. While previously programming skills were required for attacks, AI now allows anyone to create malware, exploits, and phishing campaigns effortlessly. This leads to the emergence of new, previously unseen attack scenarios that bypass traditional security measures.
The New Cyberthreat Landscape
The problem is clear: if an attack does not include known Indicators of Compromise (IoC), how can it be detected? Traditional methods — threat intelligence feeds and correlation rules — are failing to cope with the new wave of AI-driven threats. Modern attacks require a behavior-based security model: one that analyzes patterns, detects anomalies, and dynamically adapts to new threats.
How Generative AI Enables Emerging Attacks
Cyberattacks previously followed predictable patterns, exploiting known vulnerabilities or relying on classic social engineering. Today, AI-generated attacks break those patterns — allowing attackers to automate, personalize, and evolve their attack methods in real time.
Cyberattacks once required high levels of technical expertise. Now, generative AI tools can create exploits, phishing messages, and malware variants within seconds. Even individuals without technical backgrounds can now launch highly effective attacks, increasing the scale and complexity of cyber threats.
For example, AI-powered tools can generate convincing phishing emails tailored to a specific person, making them harder to detect. Polymorphic malware that constantly changes its code to evade signature detection is also possible.
Adaptive Next-Generation Attacks
Unlike pre-programmed attacks, AI-driven threats can dynamically change tactics. For example:
- Malware can rewrite its code to bypass antivirus software.
- AI-powered brute-force attacks can rotate IP addresses, device fingerprints, and login methods to mimic legitimate behavior.
- Phishing messages are hyper-personalized and can bypass spam filters.
As a result, traditional security tools are struggling to keep up with rapidly evolving AI-powered attacks.
Why Threat Intelligence and Correlation Rules Are Losing Effectiveness
For years, security teams have relied on threat intelligence and correlation rules to detect attacks. But these methods are becoming ineffective against AI-generated threats.
Threat Feeds Can’t Keep Up
Threat feeds collect known IoCs — malware signatures, IP addresses, attack patterns — and generate alerts on matches. But here’s the issue: AI-generated threats often lack known IoCs.
Because AI creates unique attacks for each target, threat intelligence feeds can’t update fast enough. Attackers easily modify code structure, execution methods, and delivery tactics — making signature-based protection ineffective.
Correlation Rules Are Too Rigid
Most security information and event management (SIEM) systems rely on predefined correlation rules. For example, a rule may trigger when a user logs in from an unusual location and downloads large amounts of data. But AI-powered attacks are so adaptive that they bypass these rigid rules.
Key weaknesses of correlation rules:
- They require constant updates — new attack methods demand new rules.
- They generate too many false positives, causing alert fatigue.
In a world of real-time evolving threats, rules simply can’t keep up.
Why UEBA Is the Best Defense Against AI Threats
To fight unknown threats effectively, organizations need a behavioral approach. That’s exactly what UEBA offers.
Behavior-Based Detection Explained
Unlike traditional methods, UEBA builds a profile of normal user or system behavior and flags deviations. This allows detection of threats even without known IoCs or predefined patterns.
UEBA can detect when:
- A user logs in from an unusual location at an odd time.
- An admin accesses files they’ve never touched before.
- A system suddenly transmits large volumes of data outside the network.
UEBA identifies subtle, progressive anomalies that other tools ignore.
How Exabeam UEBA Reduces Noise and False Positives
One of the biggest challenges in cybersecurity is alert fatigue. Exabeam solves it with two features:
- Incident grouping: UEBA stitches together multiple anomalies into a single timeline, filtering out one-off alerts.
- Dynamic risk scoring: Each anomaly receives a calculated risk score, allowing teams to focus on the most critical threats.
This way, security analysts concentrate only on what truly matters.
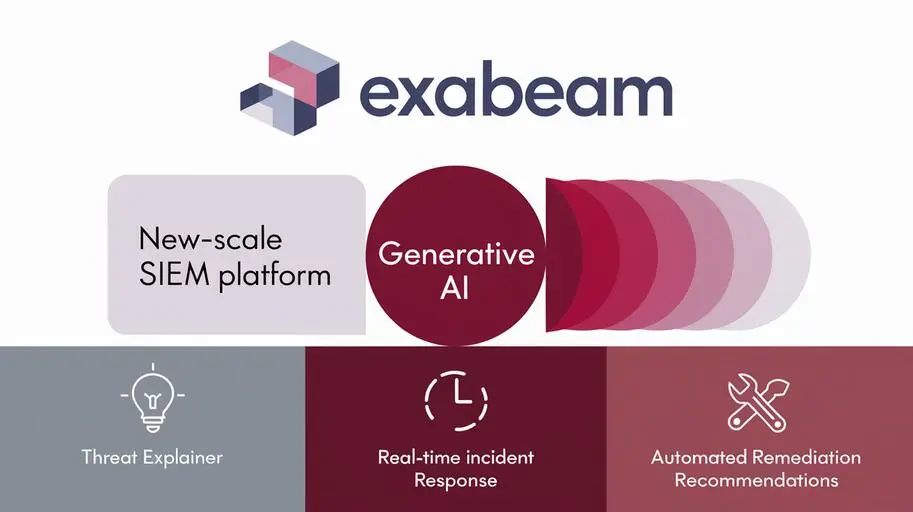
The Exabeam Advantage: A Full-Stack Security Platform
Unlike other vendors offering point solutions, Exabeam New-Scale Security Operations Platform is a complete, cloud-native security solution. It supports all key detection methods:
- Baselining: Deep understanding of normal user and system activity.
- Patented session model: Automatically correlates events into behavior-based sessions.
- Automated investigation: Simplifies analysis by grouping threats into timelines.
- Support for rules and logic trees: Combines traditional methods with UEBA.
- Open-source threat intel: Enhances behavioral analytics with known IoCs.
Exabeam New-Scale Analytics lets you detect threats in real time — without relying solely on signatures or threat feeds.
Conclusion: The Future of Cybersecurity Is Behavioral
AI-driven attacks are growing more sophisticated. Static rules and signatures are no longer sufficient. UEBA is the only approach capable of identifying unknown threats through behavioral analysis.
By deploying Exabeam New-Scale Analytics, organizations gain:
- Real-time, self-learning threat detection
- Automated user and system behavior correlation
- Precise risk scoring and reduced analyst fatigue
With Exabeam, you get the best of all worlds — threat intelligence, correlation rules, and UEBA — in a single solution.
Why Buy Exabeam UEBA from NWU?
NWU is the official distributor of Exabeam in Ukraine, the South Caucasus, and Central Asia. We offer:
- Purchase of Exabeam UEBA for modern threat protection
- Consulting on implementation and customization
- Technical support and seamless integration into your infrastructure
Contact NWU to deploy industry-leading UEBA solutions and strengthen your cybersecurity posture today!