On June 30, 2022, the BIT online conference “Cyberwar: How to Resist and Win!” gathered cybersecurity leaders to address modern challenges. Organized by CIS Events Group Ukraine, the event explored cutting-edge strategies for safeguarding businesses and critical infrastructure against the escalating threats of cyberattacks.
Netscout’s Role in Combating DDoS Threats
Netscout at BIT 2022: Expert Insights from Alexander Tomik
At the event, NWU, a trusted distributor of cybersecurity solutions, showcased its collaboration with Netscout. A highlight was the presentation by Alexander Tomik, Sales Engineer for Central and Eastern Europe at Netscout, titled “The Dark Side of DDoS: Extortion, Triple Threats, and How You’ll Be Attacked.”
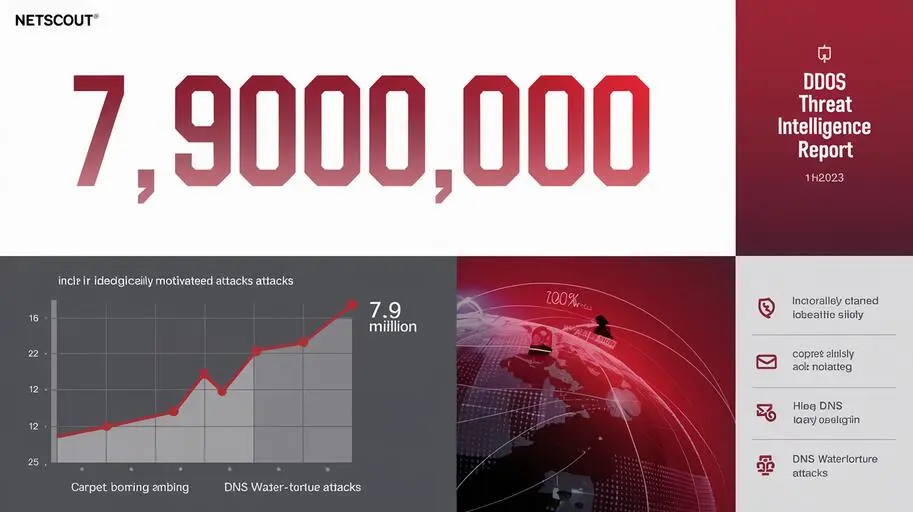
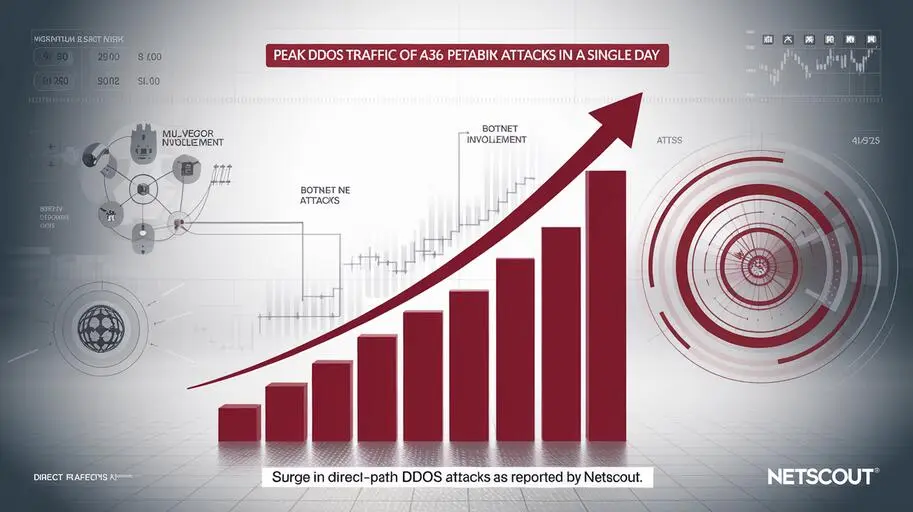
Alexander Tomik detailed how DDoS attacks have evolved into more sophisticated and destructive forms. His talk emphasized the growing complexity of DDoS campaigns and the necessity of robust, proactive defensive measures.
Exploring the Triple Threat of Modern DDoS Attacks
- Ransom-Based DDoS (RDoS): Attackers demand ransoms, threatening large-scale DDoS campaigns if payment is not made.
- Targeted Infrastructure Attacks: These aim to disable specific organizational resources, causing disruptions to critical operations.
- Multi-Vector Assaults: Combining volumetric, application-layer, and infrastructure attacks, these are particularly difficult to detect and mitigate.
Netscout Solutions for DDoS Defense
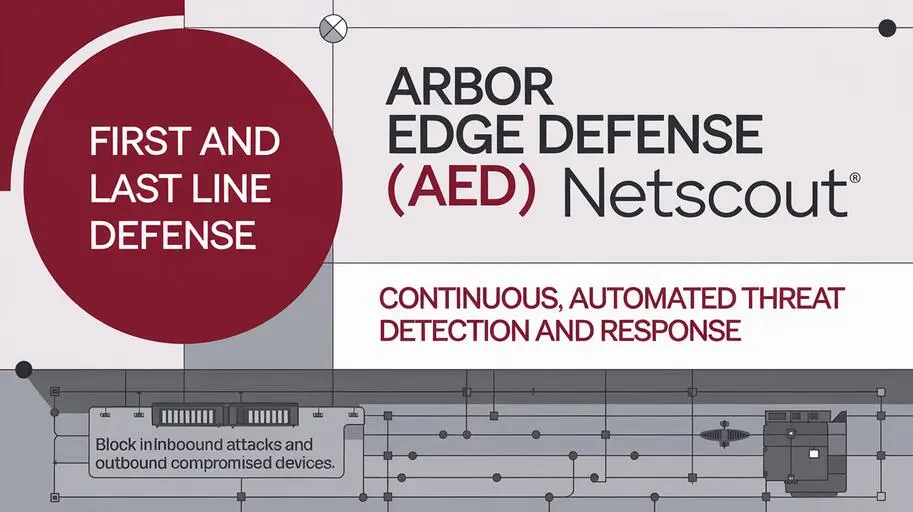
Arbor Edge Defense (AED)
Arbor Edge Defense (AED) acts as a network perimeter defense solution. It stops malicious traffic at the edge, safeguarding critical systems.
Key AED Features:
- Proactively blocks harmful traffic before it reaches vital infrastructure.
- Monitors network traffic for anomalies and threats.
- Reduces the impact of volumetric and targeted attacks.
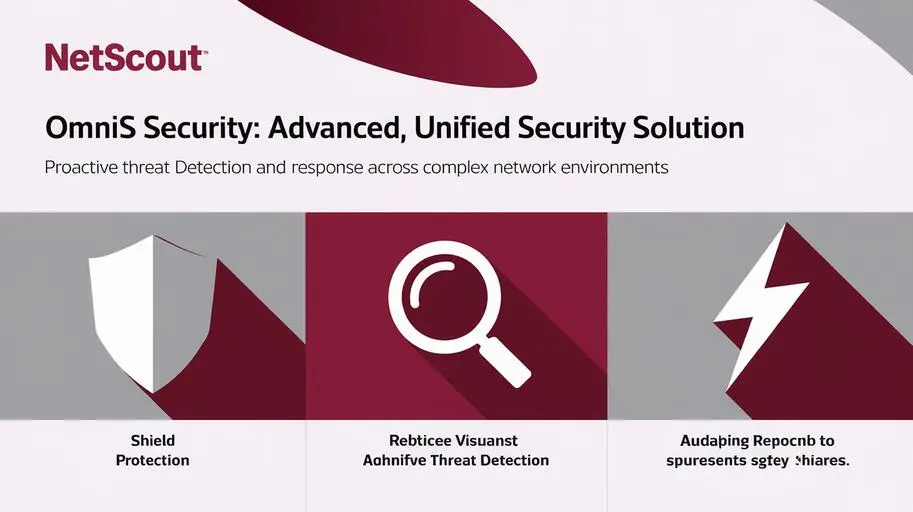
Netscout Omnis Security
Netscout Omnis Security provides deep visibility into network traffic. Using Deep Packet Inspection (DPI) and advanced analytics, it identifies threats in real time.
Omnis Security Highlights:
- Comprehensive monitoring of network activity.
- Advanced algorithms for rapid threat identification.
- Scalable architecture suitable for large enterprises.
Key Takeaways from Alexander Tomik’s Presentation
Emerging Threat Patterns
Alexander Tomik highlighted advanced tactics employed by attackers, including:
- Low-Bandwidth Attacks: Designed to avoid detection by operating below traditional thresholds.
- IoT Botnets: Leveraging connected devices for massive-scale attacks.
- Adaptive Traffic Flows: Attackers adjust patterns dynamically to bypass traditional defenses.
Leveraging Real-Time Threat Intelligence
Netscout’s solutions integrate ATLAS Intelligence Feed (AIF), a real-time database of global threat information. This enables:
- Early detection of active DDoS sources.
- Insightful trend analysis for proactive defense.
- Effective countermeasures tailored to specific threats.
Why Netscout Solutions Are Essential for Business Resilience
Mitigating the Impact of DDoS Attacks
DDoS attacks can result in:
- Service outages leading to revenue loss.
- Damaged reputation due to prolonged downtime.
- High costs associated with response and recovery.
Netscout’s solutions minimize these risks by ensuring uninterrupted operations and effective threat mitigation.
Proactive Defense with Netscout
Netscout’s tools provide:
- Dynamic Adaptation: Adjusts defenses in real time to counter changing attack strategies.
- Global Visibility: Monitors over 50% of global internet traffic for threat detection.
- Advanced Mitigation: Combines real-time analytics with machine learning to neutralize sophisticated threats.
NWU: Delivering Netscout Expertise to Key Regions
As an official distributor of Netscout, NWU brings cutting-edge DDoS protection solutions to Ukraine, Kazakhstan, and Azerbaijan. By leveraging Netscout’s advanced tools, NWU ensures businesses stay secure and operational in an era of escalating cyberwarfare.
Contact NWU today to learn how Netscout’s solutions can enhance your cybersecurity strategy.