In today’s dynamic IT landscape, companies face unprecedented cybersecurity challenges. According to a Perimeter 81 study, approximately 50% of companies with more than 1000 employees use 20 or more cybersecurity tools and solutions. This creates an enormous burden on IT teams, hindering their ability to effectively manage their networks and ensure their security. Add to this the ever-increasing number of regulatory and legislative requirements, and it becomes clear that manual management of security policies is inefficient and risky.
The more complex the network, the more time it takes to meet these requirements, especially for security teams. This problem is compounded by the large number of disparate cybersecurity tools within an organization’s network. This is where network policy automation comes to the rescue – a key tool that resolves this complexity without sacrificing flexibility, while maintaining a high level of security across on-premises, cloud, and hybrid cloud environments.
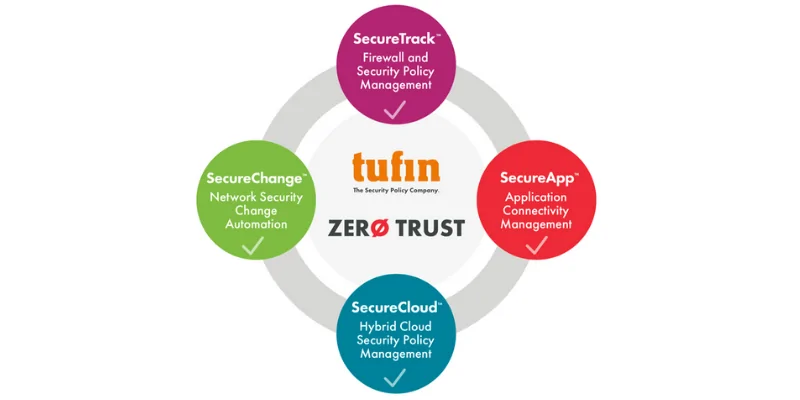
Tufin, a global leader in network security policy management and automation, offers solutions that enable organizations to automate changes to their network access security policies across their hybrid, multi-vendor environments, while maintaining compliance with industry security standards and regulatory requirements.
Why is Security Policy Automation Essential for Modern Business?
Today, more than ever before, organizations must contend with a rapidly changing IT environment, an ever-expanding attack surface, and a multitude of regulatory acts (e.g., GDPR, HIPAA, PCI DSS). Simply balancing security with flexibility is no longer enough; organizations must improve both without sacrificing business agility. Corporate networks will continue to grow in complexity, becoming poorly manageable without proper tools. This is precisely where security policy automation becomes critically important, transforming from a desirable tool into a strategic necessity.
It helps overcome the following challenges:
- Risk Reduction: Automation lowers the likelihood of human errors, which are often the cause of data breaches and vulnerabilities.
- Accelerating Changes: Policies are applied faster, allowing IT teams to respond promptly to business needs and development requirements (DevOps).
- Ensuring Compliance: Automation systems help maintain continuous compliance with regulatory requirements by providing audit trails and reports.
- Lowering Operational Costs: Optimizing routine tasks frees up IT staff resources for more strategic objectives.
How to Choose the Right Solution for Security Policy Automation?
When selecting a security policy automation solution, organizations should keep several key points in mind to ensure its effectiveness and alignment with business needs:
1. Accurate and Comprehensive Network Topology
A crucial component of any effective security policy automation tool is full and accurate awareness of the network topology. When choosing a network security automation tool, you must ensure that it is capable of “understanding” your complex and hybrid network, including both on-premises segments and dynamic cloud environments (IaaS, PaaS, Kubernetes, containers).
This is extremely important because you need accurate information for correct automation. If a solution only automates a portion of your infrastructure (e.g., 50% or less), then such a solution cannot be fully trusted. Only precise topology path calculations and policy analysis ensure the rapid and accurate provisioning of new or changed access policies. To achieve this, your policy automation solution must provide more accurate and complete network security data than your best human engineer, minimizing the risk of errors.
2. Automated Creation and Management of Security Policies
A security policy is the fundamental standard by which the quality of protection within an organization is measured. Without a clearly defined security policy, it’s difficult to gauge how well protected your organization is, and even harder to ensure consistent protection across hybrid environments. However, detecting violations of your security policy already in a production environment is a reactive, not proactive, task.
Today’s best practices encourage organizations to “shift left.” This means applying compliance checks and security policy enforcement at early stages, directly during the change process. This approach ensures that all changes made to the network are compliant and secure from the outset, before they enter the production environment.
Creating and maintaining security policies come with unique challenges. Most organizations still lack a central repository where security policies are stored and updated. Instead, administrators rely on outdated spreadsheets or institutional knowledge, which can be lost with personnel changes. Thus, policies deteriorate with organizational changes. Without a common corporate security policy serving as a single source of truth, organizations struggle to create and maintain consistent security rules. Moreover, the process of creating and implementing policies usually takes months, as administrators use various tools for their creation, and no two policies are truly identical in practice, especially in complex networks. It’s very difficult to use consistent segmentation policies across multiple disparate network security solutions.
When choosing a policy automation solution, ensure it helps you automatically create and maintain an accurate and up-to-date security policy in a hybrid environment, and makes it an integral part of your change management process. It’s important that the chosen solution can help resolve this issue, even if your organization doesn’t have a clearly defined policy before starting automation.
3. Scalability and Adaptability to a Dynamic Environment
Today, most organizations have a hybrid network, actively use IaaS and PaaS, not to mention the rapid adoption of Kubernetes and container-based development methods. This brings us to the third key point to consider when choosing a policy automation solution: it must possess exceptional scalability and adaptability to a dynamic environment.
The network and cloud environment you deal with today may differ significantly from what you will have tomorrow. A policy automation solution should easily expand as new network and cloud security management tools are added. Finding a solution that can easily scale with your company’s growth and the evolution of your IT infrastructure will save you headaches and significant costs in the future.
Today, organizations face many challenges, and policy automation solutions effectively bridge the gap between security requirements and necessary business flexibility.
Tufin Orchestration Suite – A Unique Solution in the Ukrainian IT Market in NWU’s Portfolio
Tufin Orchestration Suite is a truly advanced and unique solution from a global cybersecurity leader in the domestic IT market, represented in the portfolio of NWU, which is the official distributor of Tufin in Ukraine, Kazakhstan, Georgia, and Azerbaijan. This provides you with the opportunity to buy Tufin in Ukraine, gaining access to technologies trusted by leading global companies. Tufin Orchestration Suite is a highly desirable solution for SOC (Security Operations Center) teams of any Ukrainian company seeking to modernize its security infrastructure.
This comprehensive solution provides:
- Full visibility and control: Over all your security policies and devices in a hybrid environment.
- Automation of security processes: From change requests to their implementation and auditing, which accelerates operations and reduces workload.
- Reduced compliance costs: Through continuous compliance monitoring and automated reporting.
- Improved overall security: Through proactive vulnerability detection and automated application of correct policies.
Tufin is a trusted partner for many of the world’s largest organizations, including Fortune 500 companies and government agencies. Their trust is the best confirmation of the quality and reliability of the solution.
Why is Tufin an Investment in the Future of Your Business’s Cybersecurity?
In the evolving landscape of cyber threats, with the continuous growth in network complexity and regulatory requirements, security policy automation tools like Tufin Orchestration Suite are becoming not just a convenience, but a vital necessity.
Implementing Tufin will allow your organization to:
- Make security flexible: Adapt to rapid network changes without compromising protection.
- Reduce change time: Accelerate the implementation of new rules and applications, which is critical for DevOps and Agile methodologies.
- Ensure impeccable compliance: Automate compliance verification and reporting for various standards.
- Centralize management: Gain a single point of control over security policies across all devices and environments.
- Free up resources: Reduce the workload on the security team, allowing them to focus on strategic tasks rather than routine operations.
If you aim to optimize network security management, increase the efficiency of your IT team, and ensure compliance with the strictest requirements, Tufin Orchestration Suite is a solution worth considering. Contact NWU – the official distributor of Tufin in Ukraine, Kazakhstan, Georgia, and Azerbaijan – to receive qualified consultation and implement this advanced solution.