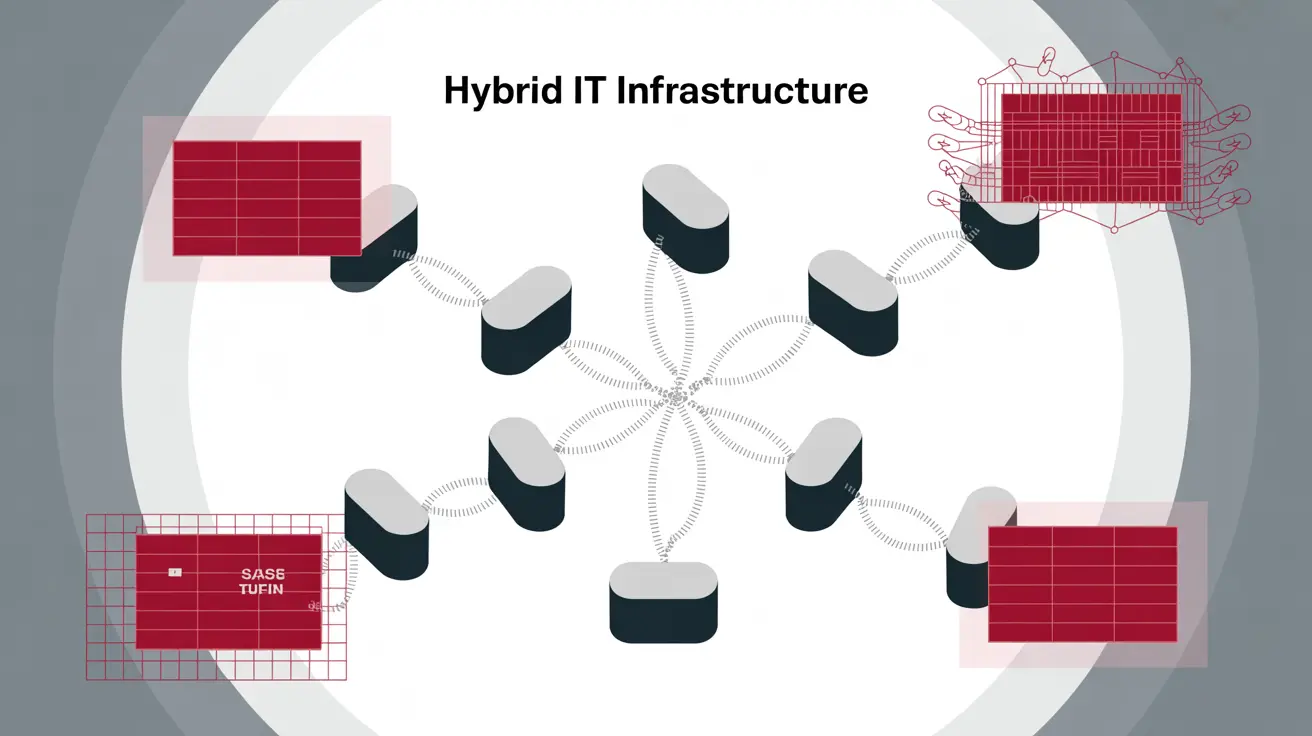
SASE (Secure Access Service Edge) is a hot topic in security today thanks to its flexible, cloud-based approach that fits perfectly with remote work. It promises to simplify access and security policy management for users, applications, and locations. However, with each new technology introduced, system complexity increases—especially in hybrid IT environments where infrastructure is partly in the cloud and partly on-premises, each with its own policies and control tools.
Why SASE Deployment Can Create Compliance Gaps—and What to Do About It
According to the 2025 Secure Network Access Report, 23% of cybersecurity professionals cite managing access policies across multiple environments as a key challenge.
This points to a transparency issue—a user may authenticate through SASE, but the traffic then passes through internal firewalls, segmentation, or cloud-based policies, and it’s unclear how well the SASE implementation aligns with them.
Policy Drift: Where the Gaps Appear
- Access is configured separately in different systems, and rules aren’t always synchronized.
- Revoking access in one environment often doesn’t reflect in another—leaving unintended access open.
- Lack of visibility makes it difficult to confirm whether policies are truly enforced as written.
How These Inconsistencies Show Up in Real Life
- A policy change request gets “stuck” in one system while the same change is already applied elsewhere.
- A new application launches without proper segmentation because the responsible team wasn’t notified.
- Teams interpret new regulations differently, logging happens in separate systems, and access reviews become a chaotic spreadsheet exercise.
How to Align Policy Without Rebuilding Every Tool
- Create a unified security model—define common policies for firewalls, cloud, and SASE so they can be applied in a single “policy language.”
- Automate changes with context awareness—include approvals, risk assessments, rollback, and cleanup in a trackable automated workflow.
- Monitor and control policy usage—identify unused or violated rules and regularly clean up the policy base.
- Unify teams—a centralized system for reviewing changes helps track where and how policies are enforced.
- Automatically document compliance—who made a change, when, and why; making audits a confirmation process instead of a reconstruction.
Conclusion
If SASE connects to data centers or the cloud, full visibility of the network path is critical. Without it, there’s fragmented control, policy chaos, and poor audit readiness. The solution starts with building a unified model, automating changes, and aligning team workflows.
Deploying SASE with Tufin
Tufin helps integrate SASE into complex hybrid environments by providing centralized visibility of networks (on-prem + cloud), policy control, and auditing—including for Zscaler. This enables you to detect and close access gaps, analyze connections, and maintain audit readiness.
Where to Buy Tufin Solutions
NWU is the official distributor of Tufin solutions in Ukraine, the South Caucasus, and Central Asia. We provide technical consulting, demos, implementation support, and post-sale assistance. By working with NWU, you gain access to innovative Tufin tools and expert support in network policy management and compliance.