In the ever-evolving world of cybersecurity, analysts face a growing volume of threats and alerts. This leads to significant workload, reduced vigilance, and consequently, the risk of missing a real attack. Can Artificial Intelligence (AI) be the solution to this problem, automating alert triage and allowing specialists to focus on what matters most?
Challenges Faced by Cybersecurity Analysts
According to surveys and observations, security analysts often highlight the same “pain points” that significantly complicate their work and lead to what is known as “alert fatigue”:
- Excessive Alert Volume: “There aren’t enough hours in the day to handle the volume of alerts on my list.” Security systems generate thousands of alerts daily, many of which are false positives.
- Difficulty Distinguishing False Positives: “I can’t use my time effectively because I can’t tell the difference between false positives and true ones.” This leads to wasted time analyzing harmless events.
- Risk of Missing Real Threats: “I’m afraid I’ll miss a real attack because the alert gets lost in the false noise of my outdated solution.” In the vast stream of alerts, it’s easy to overlook truly critical incidents.
Why Do These Problems Arise?
The main reasons for these “pain points” lie in the imperfections of traditional detection systems:
- Simplified Condition and Anomaly Matching: Many systems rely on simple rules, leading to a large number of false positives.
- Inability to Use Context: The lack of network event context analysis leads to inefficient detection. Without understanding what constitutes “normal” behavior for a specific environment, it’s difficult to distinguish benign activity from malicious.
- Emphasis on Detection, Not Organization: Most solutions focus on generating alerts but ignore the issues of their effective prioritization and triage for the analyst.
Vectra AI: Revolutionizing Alert Management with Contextual AI
Since its inception, Vectra AI has focused on creating advanced detection tools that minimize false positives. A key element of this approach is extending the capabilities of AI algorithms with network context.
Unlike traditional network security products that look for simple patterns or statistical anomalies without a deep understanding of context, Vectra AI processes detections using a wide range of network context. This allows the system to identify anomalies in a similar way an experienced security analyst would.
Practical Example: “Smash and Grab Exfil” Detection
Let’s take the example of “Smash and Grab Exfil” detection. The Vectra AI system:
- Determines Normal Data Traffic: Analyzes the normal volume of data movement for each subnet in your environment.
- Considers Popular Resources: Takes into account sites and services commonly used in your network.
- Searches for Anomalous Outbound Flows: Detects atypical outbound data flows, even in encrypted channels, which is critically important for uncovering hidden threats.
In addition, Vectra AI integrates detections across host and account entities, learning their “archetypes” and identifying each object. This allows for prioritizing detections for analysts in an actionable, ranked format, significantly simplifying work compared to competitors who simply generate detections and leave them for the analyst to sort and analyze independently.
The “True Positives” Challenge: When a Genuine Detection Isn’t Malicious
Even after minimizing false positives, there remains another important aspect – dealing with “True Positives”. The fact is, not all “True Positives” are malicious. Sometimes, behavior matches what the system indicates, in the context in which the event occurs, but it may be benign rather than malicious.
A Clear Example: Benign DNS Tunnel
Consider a case where some antivirus products embed hash lookups in DNS queries to the antivirus vendor. Such behavior can be very similar to encoding command and control (C2) channel data in a DNS payload, and that’s because it is, in essence, a true DNS tunnel. However, in this specific case, it is not malicious, but rather benign.
Vectra AI’s philosophy is to provide visibility into such high-quality detections of attacker behavior and techniques. But it’s crucial to balance this by prioritizing only highly confident, correlated detections at the host or account level for the user.
AI-Triage: Intelligent Sorting of Benign “True Positives”
This realization prompted Vectra AI to develop the AI-Triage solution. The goal was to apply some of the advanced machine learning and artificial intelligence methods used to power Vectra AI’s core algorithms to help distinguish between malicious and benign “True Positives.” The main objective was to largely eliminate the need for our customers to analyze benign “True Positives”, while prioritizing malicious ones for immediate response.
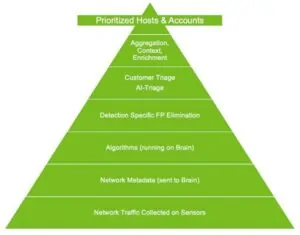
How AI-Triage Works?
AI-Triage is an integral part of the Vectra AI platform and works by:
- Automatically Analyzing Detections: AI-Triage automatically analyzes all active detections in the system.
- Using Context: The system uses the context of individual detections, as well as commonalities between detections.
- Searching for Benign Cases: The goal is to find benign “True Positives” that can be automatically triaged on behalf of the client.
Example of AI-Triage in action: If we see dozens of endpoints all generating the same hidden HTTPS tunnel detection to the same destination for at least 14 days with no other signs of compromise, we can confidently determine this to be a benign “True Positive.” AI-Triage then automatically creates a triage rule on behalf of the client, eliminating the need for an analyst to spend valuable time on it. If an analyst wishes to review it, that capability remains available in the platform, but it requires no analyst action and does not impact the host or account score.
Significant Reduction in Analyst Workload
Initially, AI-Triage support was introduced for C2 (Command and Control) and Exfil (data exfiltration) based detections, and subsequently expanded to Lateral movement detections.
The results are impressive: AI-Triage reduces the total number of detections that an analyst would otherwise have to investigate by more than 80%. This means more time can be spent on events that truly require an analyst’s attention and expertise.
AI-Triage Deployment: Simplicity and Efficiency
One of the key advantages of AI-Triage is its ease of implementation. The solution requires no customer configuration or administration.
One-Click Activation
You can activate AI-Triage capabilities by simply navigating to “Settings” -> “AI-Triage” and enabling the feature. Once enabled, AI-Triage will begin working in the background to identify highly probable benign true positives and triage them for you.
Within 30 days of its release, more than half of Vectra AI’s customers have already enabled AI-Triage, observing a significant reduction in benign True Positives. This is just the beginning of Vectra AI’s journey to enhance the efficiency of security analysts, and in future releases, AI-Triage capabilities will be expanded to cover new scenarios and other products in the company’s portfolio.
NWU: Your Cybersecurity Partner with Vectra AI in Ukraine
Thanks to NWU, the official distributor of Vectra AI in Ukraine, the domestic IT market has gained access to the advanced NDR (Network Detection and Response) solution from a global leader. NDR is an integral part of the modern SOC (Security Operations Center) triad.
NWU company is an official distributor of high-performance products and solutions in network information security and telecommunications equipment from leading global manufacturers in Ukraine, the South Caucasus, and Central Asia.
Ready to Optimize Your SOC Operations?
To purchase NDR for your SOC or to request a demo of the Vectra AI solution, please contact NWU. Learn more about how artificial intelligence can revolutionize your cybersecurity and free your analysts from routine tasks.