In today’s digital world, where cybercriminals constantly refine their methods, organizations face unprecedented challenges. Adversaries, armed with sophisticated hacking tools or stolen credentials, can easily bypass traditional perimeter network security to spy and steal assets within networks. This leads to Security Operations Center (SOC) teams being burdened with manual, time-consuming threat investigations and costly forensic analysis, often after damage has already been done to their environment.
To effectively counter these challenges, integrated solutions that provide deep visibility and automated response are needed. This is why the integration of the Vectra AI platform with Google Chronicle SIEM is critically important for modern enterprises, allowing them to move beyond reactive defense to proactive threat detection.
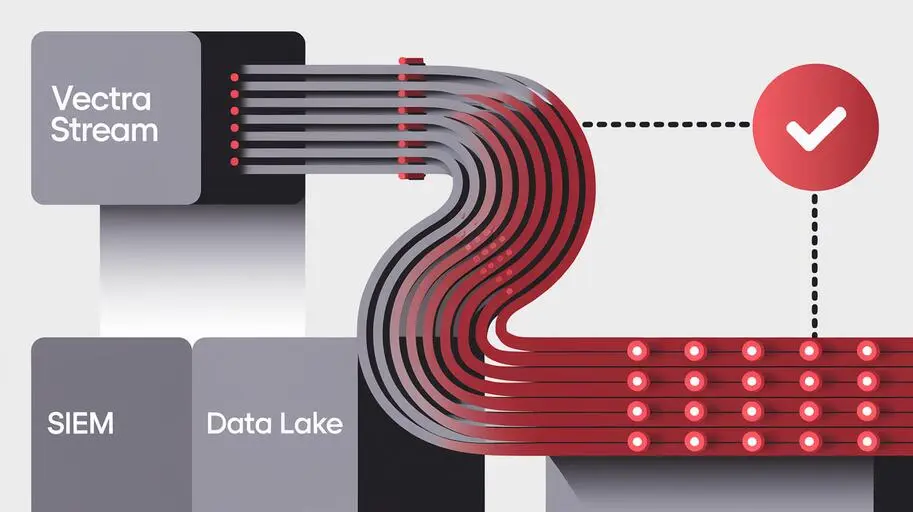
How the Vectra AI platform integrates with Google Chronicle SIEM
The Vectra AI platform, a leader in behavioral threat detection and response, combines threat hunting capabilities with incident response and investigation functions within Google Chronicle SIEM – a global security telemetry platform. This integration significantly enhances context during investigations and threat hunting through expanded operational intelligence.
By exporting metadata-enriched detections directly to the Google Chronicle SIEM dashboard, organizations can easily integrate high-value detections from Vectra AI into their existing workflows. This also enables automated correlation in Chronicle SIEM security telemetry, significantly accelerating response times. According to a SANS Institute report, automating SOC workflows can reduce incident response time by up to 70%, which is critically important for minimizing damage from cyberattacks.
Google Chronicle SIEM also captures, indexes, and correlates Vectra AI threat detections in real time, making them available in its high-performance search repository. From there, security teams can create graphs, detailed reports, set up alerts, develop specialized dashboards, and data visualizations to simplify their daily work. This allows SOC analysts to quickly detect anomalies, understand the context of an attack, and make informed decisions, transforming vast amounts of data into actionable insights.
Building better threat investigation workflows
Both Vectra AI and Google Cloud understand that organizations have many security and technology vendors in their stack. That’s why better security begins with better workflows that integrate different solutions, rather than creating fragmented data silos. Seamless integration between Vectra AI and Google Chronicle SIEM aims to build an infrastructure that allows SOC analysts to incorporate their existing workflows into robust security technologies, filling potential gaps that arise between separate security solutions.
This synergy allows for:
- Eliminating “blind spots”: Vectra AI detects hidden threats lurking in network traffic, identities, and cloud environments, providing Chronicle SIEM with critical data that might otherwise be missed. According to Microsoft, 90% of attacks begin with identity compromise, which often goes unnoticed without behavioral analysis.
- Enriching context: Detections from Vectra AI provide deep context regarding adversary behavior (tactics, techniques, procedures – TTPs), enabling Chronicle SIEM to provide more meaningful and actionable alerts. This reduces the time analysts need to understand the essence of a threat.
- Automating response: Based on Vectra AI detections, SOC teams can configure automated response actions in Chronicle SIEM, such as blocking malicious IP addresses, isolating infected hosts, or suspending user accounts. This enables instant response to critical threats, minimizing potential damage.
- Optimizing threat hunting: Analysts can use the advanced search capabilities of Chronicle SIEM to more quickly detect complex attacks, utilizing the details of detections from Vectra AI. This transforms proactive threat hunting from a routine task into a highly effective process.
- Reducing “alert fatigue”: Thanks to highly accurate detections from Vectra AI, which focus on real threats, the number of false positives in Chronicle SIEM is significantly reduced. This allows analysts to focus on truly important incidents, increasing their effectiveness and reducing the risk of burnout.
Why Vectra AI behavioral analysis is critical for SIEM
Traditional SIEM systems, while powerful tools for collecting and aggregating logs, often face the problem of “alert overload” and an inability to detect new or sophisticated attacks. This is because they primarily rely on signature-based analysis and correlation of known events. According to Cybersecurity Ventures, by 2025, global cybercrime damages will reach $10.5 trillion annually, highlighting the need for more advanced protection methods.
In contrast, Vectra AI uses advanced artificial intelligence and behavioral analysis to detect unknown threats and zero-day attacks. The Vectra AI platform tracks adversary TTPs (tactics, techniques, and procedures), allowing it to identify attacks even when their tools or methods change. This complements the capabilities of Google Chronicle SIEM, providing it with the “intelligence” to detect complex, hidden threats that might slip past other security measures.
For example, if Vectra AI detects lateral movement within the network or anomalous access to file resources using legitimate credentials (which is a typical phase of sophisticated attacks), it sends this highly contextual data to Chronicle SIEM. This allows SOC teams to quickly understand what is happening, even if the access itself was “legitimate” from the perspective of traditional security rules, but the behavior was anomalous.
Vectra AI – a valuable asset for cybersecurity in Ukraine via NWU
In the current context of constantly escalating cyber threats and the need to ensure a high level of cyber resilience, Vectra AI solutions are strategically important for Ukrainian organizations. The war in Ukraine has significantly increased the level of cyberattacks, making reliable protection a critical necessity.
Vectra AI is a powerful solution that can help organizations defend against the most complex attacks, including those leveraging GenAI capabilities. Thanks to its ability to accurately and quickly detect GenAI-driven attacks, as well as provide comprehensive visibility and ease of use, the Vectra AI platform is a valuable addition to any cybersecurity program.
Vectra AI is a leader in detecting and responding to hybrid cloud threats based on security artificial intelligence. Only Vectra optimizes artificial intelligence to detect adversary methods — TTP (Tactics, Techniques, and Procedures), which are the foundation of all attacks — instead of simply alerting about “anomalies” or “other” events. The resulting highly accurate threat signal and clear context allow cybersecurity teams to quickly respond to threats and prevent attacks from escalating into full-blown breaches.
The Vectra AI platform and services cover public cloud, SaaS applications, identity systems, and network infrastructure, both on-premises and in the cloud. Organizations worldwide rely on the Vectra AI platform and services to achieve resilience against: ransomware, supply chain compromise, credential theft, and other cyberattacks.
Thanks to NWU, the official distributor of Vectra AI in Ukraine, it is now possible for the domestic IT market to buy NDR (Network Detection and Response) from a global leader. NDR is an integral part of the SOC triad alongside SIEM and EDR, providing a full cycle of threat detection and response. This allows Ukrainian enterprises to significantly enhance their level of cybersecurity and more effectively counter modern threats, which is especially relevant in the context of hybrid warfare.
Equip your SOC with advanced threat detection and automated response capabilities. To buy NDR for SOC or request a demo of the Vectra AI solution in Ukraine, contact NWU today.