As we approach 2022, two major and concerning trends have become evident in the world of cybersecurity. Firstly, cyberattacks are no longer exclusively targeting small to medium-sized businesses with limited SOC resources, which historically faced the most pressure in this area. Even large organizations and government structures are now common targets. This has become an everyday reality, as evidenced by the increasing number of high-profile incidents such as ransomware attacks on critical infrastructure, data breaches from multinational corporations, and state-sponsored cyber espionage. According to the IBM Cost of a Data Breach Report 2021, the average cost of a data breach reached a record $4.24 million, highlighting the severity of the problem.
Secondly, preventative defense strategies based solely on traditional perimeter solutions are no longer sufficient. This is exacerbated by the malicious use of Artificial Intelligence (AI) and Machine Learning (ML) by adversaries to find and execute effective attack vectors. AI has rendered many older security tools, such as firewalls and classic SIEM solutions, less effective because they are unable to adapt quickly to rapidly changing attack tactics, techniques, and procedures (TTPs).
However, a third trend offers optimism – artificial intelligence is also working for cyber defense. In fact, in current realities, if you are not using AI to protect your organization, it will not be optimally secured. AI has become our primary ally in building a secure future, offering unprecedented capabilities for detecting, analyzing, and neutralizing the most sophisticated cyber threats.
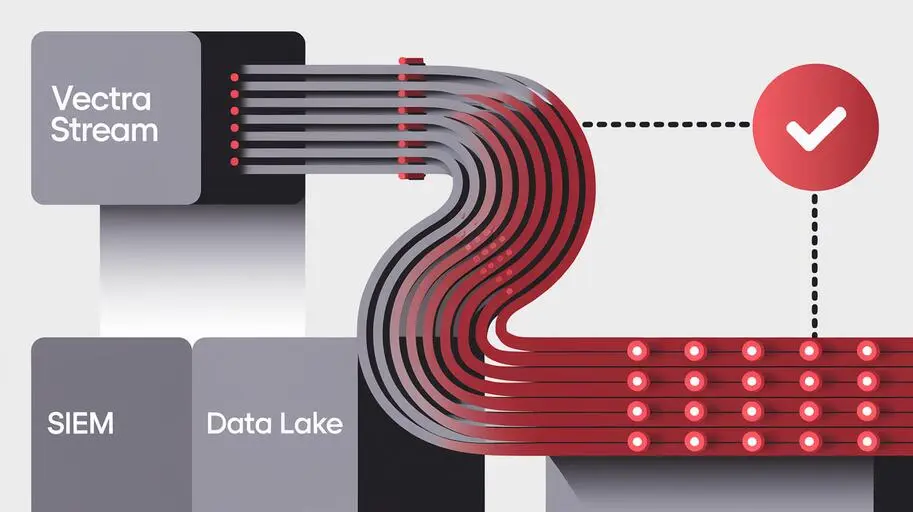
Currently, the most effective AI-powered cybersecurity solution is the Cognito platform from Vectra AI – a global leader in the NDR (Network Detection and Response) market, providing tools for detecting threats in network traffic and responding to them in real-time.
Adversaries Inevitably Infiltrate Your Systems
A cyberattack leveraging AI can instantly change its attack vector, adapting to defensive mechanisms. A modern enterprise is a complex and distributed ecosystem, including cloud networks, disparate workplaces, and numerous personal devices. All of this creates too many potential entry points. Ultimately, a motivated, experienced, and persistent attacker will always find a way inside your system. There are many available paths, from phishing attacks and vulnerability exploitation to credential compromise.
The first and traditional line of defense – the company’s firewall – is insufficient for protecting against threats that utilize artificial intelligence and constantly change their behavior patterns. In many ways, a firewall is similar to a seasonal flu shot, effective against a specific virus. Standard protection will not work against an advanced, experienced attacker and only creates a false sense of security, as it cannot detect “horizontal” movement of the attacker within the network after initial penetration.
To mitigate the consequences of inevitable breaches, we need to change our mindset. The real security solution lies in accepting the fact that penetrations are inevitable and will occur, and focusing efforts on minimizing the damage, reducing it to relatively minor inconveniences rather than catastrophic consequences. This requires a shift from a “prevent everything” paradigm to a “rapid detection and response” model.
Finding the “Needle in a Haystack”
Assuming that hackers will find their way into the target system one way or another, the next question arises – how to find the proverbial “needles in a haystack”? This task has historically fallen to SIEM (Security Information and Event Management) solutions. But one haystack is a poor metaphor for a modern enterprise. It’s more like an entire farm, where data flows from various sources: from the cloud to IoT devices, different users, and their devices. The sheer volume of resources and connections significantly complicates the situation. Sending all your data to a SIEM and hoping for the detection of correlated threats is no longer an effective defense.
Unfortunately, the reality is that most SIEM deployments are simply expensive log collection solutions that don’t meet modern requirements. Even when organizations can cope with all the soft costs of SIEM (including license fees, maintenance, and analyst staffing), the reality is that SIEM correlation alone cannot cope with the task of enterprise protection. This is due to the colossal volume of data generated, the complexity of configuring correlation rules, and the constant need for signature updates.
SIEM is increasingly being displaced by optimized threat detection and response solutions based on AI and machine learning, which are better equipped to solve modern security problems. Ultimately, why reinvent the wheel with SIEM when modern effective alternatives are faster, better, and often cheaper in the long run?
Vectra Cognito’s AI-powered detection methods can perform analysis at a speed and scale simply unattainable by a human, demonstrating high accuracy and useful effectiveness. By leveraging AI-driven behavioral models and machine learning, the Cognito threat detection and response platform enhances detection capabilities far beyond what SIEM can offer.
Vectra AI’s AI-based security solutions allow for precise identification of compromised assets by logging telemetry from the cloud and other sources, analyzing threats, and accurately interpreting metadata from packets collected across the network. This includes the analysis of East-West traffic, which is critically important for detecting lateral movement of attackers within a compromised network.
Unlike SIEM-based solutions, AI can navigate environments and track attacks by observing real-time cloud and network behavior, providing timely and high-quality security analytics. This makes AI a candidate for performing defensive tasks previously envisioned for SIEM (and a significant number of new ones), with greater efficiency and lower management and maintenance costs.
Vectra Cognito AI – The New Hero in Cybersecurity
The combined use of AI and the cloud allows for the detection of sophisticated and subtle attack tactics, such as hiding malware within legitimate traffic. Recognizing such rapid malicious actions is beyond practical manual analysis. It requires significant prior knowledge of the attack type and location, which is usually unavailable. Static signatures can only point to specific instances of known threats, but the Vectra Cognito artificial intelligence platform can automatically detect hidden attacker behavior and ongoing threats, and respond instantly to prevent ongoing threats from becoming data sources.
To aid in AI training, threat researchers identify targeted threat behaviors and provide examples. Data scientists create and test models, and together they compile datasets to train behavioral models. Thanks to these resources, the Vectra Cognito artificial intelligence toolkit is well-equipped to recognize known patterns and quickly detect threats.
Even greater value is represented by the deployment of unsupervised artificial intelligence models that learn solely based on direct local observation. By gaining access to anonymized security metadata from multiple companies using the same platform, the Vectra Cognito AI-based solution uses neural networks for autonomous analysis and detection of hidden malicious indicators, learning to distinguish what “normal” traffic looks like. By utilizing vast amounts of anonymous/encrypted traffic data via the cloud, AI learns the differences between normal and malicious activity entirely independently, without human intervention, making it extremely effective in detecting zero-day attacks and unknown threats.
Cyberattacks are now a new reality, but the current damage from them can be reduced in the future if we change our mindset and attitude towards them. We need to stop thinking about “preventing cyberattacks” or “protecting against intruder penetration.” Prevention is a losing strategy if it is not complemented by reliable detection and response mechanisms.
However, for an attacker, the task of collecting valuable information inside a system can become much more difficult than merely penetrating its environment. A well-trained, automated NDR cybersecurity solution like Vectra Cognito with artificial intelligence can significantly complicate the task for cybercriminals, reducing the damage from their actions and the likelihood of a ransom payment to zero. This is achieved through prompt detection of suspicious activity, blocking attacker communications, and providing SOC teams with accurate, contextualized information for rapid response.
Vectra AI – A Valuable Asset from NWU for Ukraine’s Cybersecurity
Vectra AI is a powerful solution that can help organizations protect themselves from GenAI-based attacks. Thanks to its ability to accurately and quickly detect GenAI-attacks, as well as provide visibility and ease of use, the Vectra AI platform is a valuable addition to any cybersecurity program.
Thanks to NWU, the official distributor of Vectra AI in Ukraine, it is now possible for the domestic IT market to purchase NDR (Network Detection and Response) from a global leader, which is an integral part of the SOC triad. The SOC triad represents a combination of key security technologies: SIEM (Security Information and Event Management), EDR (Endpoint Detection and Response), and NDR. This synergy allows for the creation of a comprehensive cyber defense system that provides full visibility, deep analysis, and rapid response to threats at all levels of the infrastructure.
Vectra AI is a leader in detecting and responding to hybrid cloud threats based on security artificial intelligence. Only Vectra optimizes AI to detect attacker methods — TTP (Tactics, Techniques, and Procedures), which are the foundation of all attacks — instead of simply alerting on “other” anomalies. The resulting high-fidelity threat signal and clear context enable cybersecurity teams to react quickly to threats and prevent attacks from escalating into system breaches.
Vectra AI Platform and Services Cover:
- Public Cloud: Ensuring the security of data and applications in public cloud environments (such as AWS, Azure, Google Cloud Platform), where traditional security tools often face visibility challenges.
- SaaS Applications: Protection against threats that exploit software-as-a-service vulnerabilities, which is particularly relevant given the widespread use of cloud applications.
- Identity Systems: Monitoring and detecting the compromise of credentials and privileged access, which are common targets for attackers.
- Network Infrastructure: Comprehensive protection for both on-premises and cloud networks, ensuring continuous visibility and control.
Organizations worldwide rely on the Vectra AI platform and services to achieve resilience against:
- Ransomware: Rapid detection and blocking of ransomware activity in the early stages of an attack, minimizing damage from data encryption.
- Supply Chain Attacks: Detecting anomalies in vendor behavior or integrated components that may indicate hidden threats.
- Credential Theft: Identifying attempts to steal or use compromised credentials for unauthorized access.
- Other Cyberattacks: Providing protection against a wide range of current and future threats, including fileless attacks, “zero-day” attacks, and targeted APT (Advanced Persistent Threats) group attacks.
Strengthen Your SOC with Vectra AI and NWU
Modern cyber threats demand innovative approaches to security. Vectra AI solutions based on artificial intelligence offer unparalleled detection accuracy and automation of response, which is critically important for any SOC.
To purchase NDR for your SOC or to order testing of the Vectra AI solution in Ukraine, please contact NWU. As an official distributor, we offer not only advanced technologies but also expert support that will help you most effectively implement and utilize this powerful solution. This is your chance to significantly enhance the effectiveness of your security team and reliably protect your digital assets.
NWU is an official distributor of highly effective products and solutions in network information security and telecommunication equipment from leading global manufacturers. We operate in Ukraine, the South Caucasus, and Central Asia.
Among our solutions are:
- Anti-DDoS from NETSCOUT (formerly Arbor Networks) – protection against distributed denial-of-service attacks that can paralyze service operations.
- SIEM and UEBA from Exabeam and LogRhythm – security information and event management systems, as well as user and entity behavior analytics for anomaly detection.
- Firewall Policy Management from Tufin – managing firewall security policies, ensuring compliance and minimizing errors.
- NDR from Vectra AI – highly effective network threat detection and real-time response.
- SBC and UC from Ribbon Communications – solutions for protecting unified communications and call sessions.
- EDR, EPP, NDR, and XDR from Cynet – a comprehensive platform for endpoint protection, network, and extended threat detection.
- Storage Systems (SDS) from Infinidat – high-performance and reliable solutions for storing large volumes of data.
- And innovative environmental monitoring solutions from Huma-I, Nuvap, Sensibo, uHoo, and others – to ensure physical security and comfort.
Learn more on the vendor’s website: https://www.vectra.ai/